Secure Setup¶
Kinetica uses a packaged Apache HTTPD proxy solution, which should be managed via Kinetica. Kinetica uses core configuration values to generate Apache proxy settings and start the HTTPD service as part of the Kinetica stack. LDAP setup documentation is available for the following external authentication providers:
- LDAP (e.g., OpenLDAP)
- Microsoft Active Directory
The diagram below outlines how the secure setup works; red arrows are SSL/HTTPS connections, gray arrows are unsecure/HTTP connections, and blue arrows could be either secure or unsecure depending on your LDAP setup.
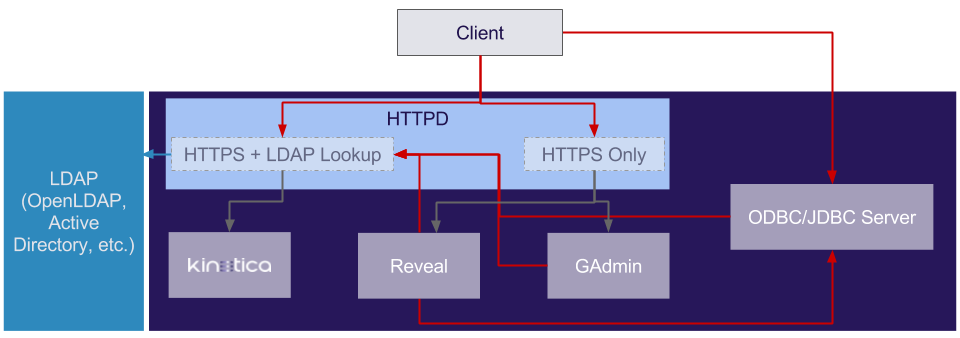
HTTPD Secure Setup
Enabling HTTPD, SSL, and LDAP¶
Kinetica can be configured to communicate with an LDAP server, such as OpenLDAP or Active Directory, but first you'll need to update Kinetica to talk with LDAP.
Prerequisites¶
Ensure the LDAP instance is running and properly configured
Ensure GAdmin has been initialized per the instructions found in Validate the Installation and the default username and password have been updated
Ensure a corresponding external user is created for each user in your LDAP solution and that each user is a member of the proper roles, or use the
auto_create_external_usersparameter (see Database Configuration). See Security Concepts and Security (User/Role Management) for more information on external usersEnsure a valid SSL key and certificate have been created. It is recommended you create them in
/opt/gpudb/certsEnsure an SSL certifcate has been added to OpenSSL's trust store (for more information, go here):
ln -s <path/to/cert.pem> `openssl x509 -hash -noout -in <path/to/cert.pem>`.0
Import an SSL certificate into a Java truststore using the following command:
keytool -import -trustcacerts -file <path/to/cert/file> -alias cert_alias -keystore <desired/path/for/keystore.jks>
Stop the database using GAdmin or
service gpudb stop
Database Configuration¶
You can read more about the various settings in the database config file here.
Navigate to
/opt/gpudb/core/etc/gpudb.confand update head_ip_address as necessaryOptionally, update the following setting to remove the default value (
*). This setting update is necessary for applications that depend on Kinetica for data:http_allow_origin = *
Update the following setting to
trueenable_httpd_proxy = true
Update the following settings. Read Security Configuration for more information
# Require authentication. require_authentication = true # Enable authorization checks. enable_authorization = true
Update the following settings to
true# IMPORTANT: DO NOT ENABLE unless external access to GPUdb ports # has been blocked via firewall AND the authentication proxy is # configured to block REMOTE_USER HTTP headers passed in from clients. enable_external_authentication = true # Automatically create accounts for externally-authenticated users. # If enable_external_authentication is false, this setting has no effect. # Note that accounts are not automatically deleted if users are removed # from the external authentication provider and will be orphaned. auto_create_external_users = true
ODBC Configuration Files¶
Important
Depending on how you installed ODBC, there may be
other odbc.ini files available on your system that
could override Kinetica's System DSNs. Kinetica's
System DSNs are located in
/opt/gpudb/connectors/odbcserver/client/etc/odbc.ini
Navigate to the proper
odbc.inifile and update the following settings (for all DSNs)SSLCACertFile=<path/to/cert/file> UseSsl=1
Optionally, add the following settings. Read more about the settings here:
AllowHostMismatch=1 AllowSelfSignedCert=1 AllowExpiredCert=1
Navigate to
/opt/gpudb/connectors/odbcserver/bin/gpudbodbc.iniand update the following settings, ensuring you replace the SslCertfile and SslKeyFile setting values with the proper file paths to the ODBC server's private key and private certificate respectively:UseSsl=1 SslCertfile=<path/to/cert/file> SslKeyFile=<path/to/key/file>
Update the
URL, addinghttpsand ensuring the host is correct for your setupURL=https://<hostname>:8082/gpudb-0
Optionally, update the
CertPathsetting if your SSL certificate and key are not in the default location:CertPath=/opt/gpudb/certs
Optionally, change the
SslAllowHostMismatchsetting to1if you don't want to enforce host matching when using SSL between ODBC and Kinetica:SslAllowHostMismatch=0
Optionally, update the
UIDandPWDsettings. Ifrequire_authenticationisfalseandenable_authorizationistrue, add credentials for a guest account role with different permissions than the Public role. If bothrequire_authenticationandenable_authorizationaretrue, add credentials to enable a guest account. Note there has to be an account that matches the givenUIDandPWDsettings:UID= PWD=
Important
Leave the UID and PWD settings blank to ensure a
completely secure setup.
HTTPD "Data" Configuration¶
Note
If you are not using HTTPS with HTTPD, but you are using HTTPS
with Kinetica, then only uncomment SSLProxyEngine On and add
SSLProxyMachineCertificateFile </path/to/cert>
Navigate to
/opt/gpudb/httpd/conf/data.confand uncomment the following settings, ensuring you replace the SSLCertificateFile and SSLCertificateKeyFile setting values with the proper file paths. Read the Apache HTTPD SSL Docs for more informationSSLEngine On ... SSLCertificateFile </path/to/cert> SSLCertificateKeyFile </path/to/key> SSLProxyEngine On RequestHeader set X-Forwarded-Proto "https"
Important
The following settings are optional but provide greater security.
Depending on what version of OpenSSL is installed on the
system, the TLS version should be updated. The
SSLCipherSuite setting can also be upgraded, e.g.,
SSLCipherSuite HIGH:!aNULL:!MD5:
SSLProtocol -all +TLSv1.1
SSLCipherSuite HIGH:MEDIUM
Header edit Set-Cookie ^(.*)$ $1;HttpOnly;Secure
Header set Access-Control-Allow-Methods "POST, GET, OPTIONS, DELETE, PUT"
Header set Access-Control-Max-Age "1000"
Header set Access-Control-Allow-Headers "x-requested-with, Content-Type, origin, authorization, accept, client-security-token"
HTTPD "NoAuth" Configuration¶
Navigate to
/opt/gpudb/httpd/conf/noauth.confand uncomment the following settings, ensuring you replace the SSLCertificateFile and SSLCertificateKeyFile setting values with the proper file paths. Read the Apache HTTPD SSL Docs for more informationSSLEngine On ... SSLCertificateFile </path/to/cert> SSLCertificateKeyFile </path/to/key> SSLProxyEngine On RequestHeader set X-Forwarded-Proto "https"
Important
The following settings are optional but provide greater security.
Depending on what version of OpenSSL is installed on the
system, the TLS version should be updated. The
SSLCipherSuite setting can also be upgraded, e.g.,
SSLCipherSuite HIGH:!aNULL:!MD5:
SSLProtocol -all +TLSv1.1
SSLCipherSuite HIGH:MEDIUM
Header edit Set-Cookie ^(.*)$ $1;HttpOnly;Secure
Kinetica Components Configuration¶
After enabling LDAP and HTTPD, you'll need to reroute all Kinetica components to use the new HTTPD port (8082). Follow the sections below to update each component included with Kinetica.
GAdmin¶
Navigate to the
/opt/gpudb/tomcat/webapps/gadmin/WEB-INF/classes/gaia.propertiesfile and update the following settings forhttps, ensuring the host is correct for your setupgpudb_ext_url = https://<hostname>:8082/gpudb-0 ... gpudb_ext_hm_url = https://<hostname>:8082/gpudb-host-manager
Navigate to the
/opt/gpudb/tomcat/conf/catalina.propertiesfile and add the following settings to the bottom of the file, ensuring you replace thetrustStoresetting value with the proper file path and thetrustStorePasswordsetting with the correct passwordjavax.net.ssl.trustStore=</path/to/keystore> javax.net.ssl.trustStorePassword=<your-keystore-password>
Important
A keystore being added to catalina.properties will
prevent security settings from being overwritten during a
Kinetica upgrade
Reveal¶
Note
The AUTH_USER_REGISTRATION_ROLE setting in the
config.py file can correspond to any role as long as the
role is available in Reveal.
Navigate to
/opt/gpudb/connectors/reveal/etc/config.pyand confirm that the following setting is set toTrue.ENABLE_PROXY_FIX = True
Update the following setting to
True.ENABLE_DB_AUTH = True
Uncomment the following settings.
# Will allow user self registration AUTH_USER_REGISTRATION = True # The default user self registration role AUTH_USER_REGISTRATION_ROLE = "Dashboard"
Navigate to
/opt/gpudb/connectors/reveal/etc/default.jsonand update the following settings:"gadmin": { "url": "https://localhost:8443/gadmin" },
Enable user auto creation.
"auth": { "autocreateuser": true, ...
Integrating with External User Data Stores¶
LDAP¶
The following instructions will help you setup Kinetica and HTTPD to work with LDAP, e.g., OpenLDAP.
Note
Kinetica comes packaged with an instance of OpenLDAP. Read more about how to use it on here.
HTTPD "Data" Configuration¶
Navigate to
/opt/gpudb/httpd/conf/data.conf, uncomment the following settings, and update them as necessary. Read more about the HTTPD LDAP settings here.## The following is an example configuration for authenticating Kinetica ## users against an LDAP server. Please refer to the Apache httpd ## configuration manual for assistance. Note that in order to use LDAP ## authentication, enable_external_authentication must be set to true in ## gpudb.conf. AuthName "Kinetica Authentication" ## LDAP server URL and full LDAP path to users directory with search ## parameters. If an attribute other than "uid" is used for the user ID, ## update it below. AuthLDAPUrl ldap://127.0.0.1:9009/dc=gpudb,dc=com?uid?sub ## Valid LDAP user to use for search during bind AuthLDAPBindDN cn=admin,dc=gpudb,dc=com ## Password of user for search during bind AuthLDAPBindPassword admin # Clear the REMOTE_USER and KINETICA_ROLES headers, so that they # cannot be passed through by the client. Header unset REMOTE_USER Header unset KINETICA_ROLES AuthType Basic ## The following (AuthBasicAllowAnonymous) is a custom httpd configuration ## parameter which will allow failed LDAP lookups to trickle through to ## GPUdb, where it can attempt an internal authentication and/or reach ## endpoints without credentials if auth is not required. This can be ## turned off when internal users are not being used, and no anonymous ## access is desired. AuthBasicAllowAnonymous on AuthBasicProvider ldap AuthzLDAPAuthoritative on <LimitExcept OPTIONS> Require valid-user </LimitExcept> ... ## Add REMOTE_USER and KINETICA_ROLES HTTP headers, and do not pass ## through any AUTHORIZATION header containing LDAP credentials. Update ## the first line below if an attribute other than "uid" is used for the ## user ID. RequestHeader set REMOTE_USER %{AUTHENTICATE_uid}e env=AUTHENTICATE_uid RequestHeader set KINETICA_ROLES %{KINETICA_ROLES}e env=KINETICA_ROLES RequestHeader unset AUTHORIZATION env=AUTHENTICATE_uidImportant
If you have groups you want to map to Kinetica roles, uncomment and add the mappings above the
RequestHeadersection.
Microsoft Active Directory¶
The following instructions will help you setup Kinetica and HTTPD to work with Active Directory.
HTTPD "Data" Configuration¶
Navigate to
/opt/gpudb/httpd/conf/data.conf, uncomment the following settings, and update them as necessary, ensuring you replace any instances ofuidwithsamaccountname. Read more about the HTTPD LDAP settings here.## The following is an example configuration for authenticating Kinetica ## users against an LDAP server. Please refer to the Apache httpd ## configuration manual for assistance. Note that in order to use LDAP ## authentication, enable_external_authentication must be set to true in ## gpudb.conf. AuthName "Kinetica Authentication" ## LDAP server URL and full LDAP path to users directory with search ## parameters. If an attribute other than "uid" is used for the user ID, ## update it below. AuthLDAPUrl ldap://127.0.0.1:9009/dc=gpudb,dc=com?samaccountname?sub ## Valid LDAP user to use for search during bind AuthLDAPBindDN cn=admin,dc=gpudb,dc=com ## Password of user for search during bind AuthLDAPBindPassword admin # Clear the REMOTE_USER and KINETICA_ROLES headers, so that they # cannot be passed through by the client. Header unset REMOTE_USER Header unset KINETICA_ROLES AuthType Basic ## The following (AuthBasicAllowAnonymous) is a custom httpd configuration ## parameter which will allow failed LDAP lookups to trickle through to ## GPUdb, where it can attempt an internal authentication and/or reach ## endpoints without credentials if auth is not required. This can be ## turned off when internal users are not being used, and no anonymous ## access is desired. AuthBasicAllowAnonymous on AuthBasicProvider ldap AuthzLDAPAuthoritative on <LimitExcept OPTIONS> Require valid-user </LimitExcept> ... ## Add REMOTE_USER and KINETICA_ROLES HTTP headers, and do not pass ## through any AUTHORIZATION header containing LDAP credentials. Update ## the first line below if an attribute other than "uid" is used for the ## user ID. RequestHeader set REMOTE_USER %{AUTHENTICATE_samacccountname}e env=AUTHENTICATE_samaccountname RequestHeader set KINETICA_ROLES %{KINETICA_ROLES}e env=KINETICA_ROLES RequestHeader unset AUTHORIZATION env=AUTHENTICATE_samaccountnameImportant
If you have groups you want to map to Kinetica roles, uncomment and add the mappings above the
RequestHeadersection.
Logging In Securely¶
Update your firewall settings to allow HTTPD passthrough and to disable all incoming ports. See either Adjust the Firewall (RHEL) or Adjust the Firewall (Debian/Ubuntu) for more information
After adjusting your firewall, restart the database using:
service gpudb start
Verify both internal and exteral users can login to Kinetica Administration Application (GAdmin) at
http://<host-ip>:8080Verify both internal and external users can login to Reveal at
https://<hostname>:8444/caravel/connectVerify both internal and external users can use isql:
isql -v <DSN name> <username> <password>
